Key Features
- Enterprise Risk Rating
- Inventory Validation
- External Footprint Identification
- Dozens of Data Points Returned
- Wide and Deep Detection
- Actionable Information
- Robust API
- Easy to Use/Understand
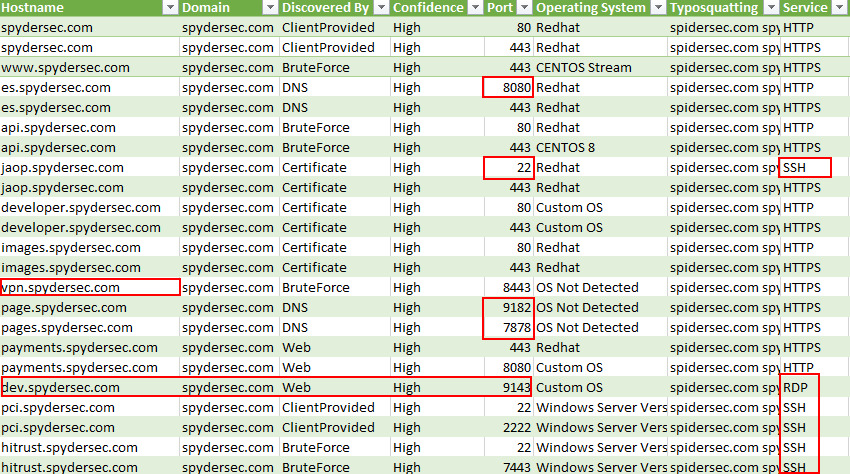
The results are highlighting open ports, external attack surface, overlooked remote administration access, and even misconfigurations showing the potential leakage of employee usernames.